Why Your DNS Infrastructure Should Support Dual-Protocol
In this installment of the Infoblox IPv6 Center of Excellence (COE) blog series, we will examine why organizations should make their public authoritative nameservers communicate using both IPv4 and IPv6. This has been the advice of experienced network architects for many years, but others may not be aware of why this would be an advantageous […]
Pros and Cons of Cloud DNS Services
As more organizations move to the cloud for Domain Name System (DNS) services, the global DNS services market is now valued at more than $215M, with continued growth expected.
IPv6 DNS Queries: A Work in Progress
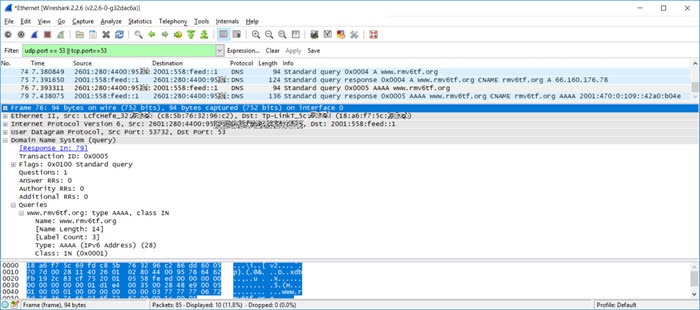
Imagine what it was like to be an ancient mariner navigating the ocean blue at night using nothing more than stars, a sextant and a marine chronometer. Thankfully, navigating the Internet is not as daunting. The method that networked devices use to find their way around the digital ocean is the Domain Name System (DNS), […]
Why Router-Based DHCP Won’t Work With IPv6
There are many enterprise companies who are still using DHCP for IPv4 on their routers/switches. This is typically done by the network administrator who needs to get a DHCP capability up and running quickly but does not have access to a DHCP server. More often than not, this is done by an IP Telephony engineer […]
Improved TLS / SSL Security with DANE
You may be familiar with the benefits of using DNSSEC to provide authentication and integrity for your DNS information. DNSSEC is a lot like dental floss: we all know that it is good for our health, but few enterprise organizations actually put forth the effort to implement the best practice. If organizations do not use […]
Improved Network Security through DNS Inspection (Pt. 1)

Virtually all networked applications use Internet Protocol (IP) communications and rely extensively on the Domain Name System (DNS) to determine the IP address to connect. DNS provides the mapping of human-readable fully-qualified host names to IP addresses. If you inspect the DNS queries taking place over a network you can gain an understanding of which […]
Improved Network Security through DNS Inspection (Pt. 2)
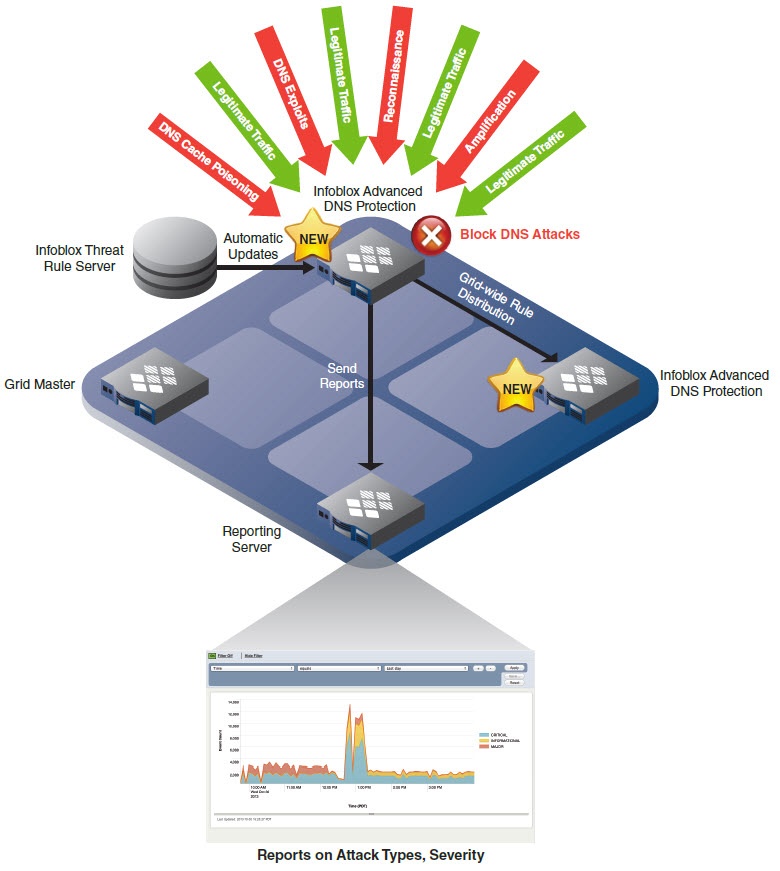
In the previous blog post on DNS traffic inspection we covered how attackers target DNS systems. Attackers use Fast-Flux DNS techniques to rapidly change the server’s hosting malware. Attackers control malware to change the DNS behavior on the end-user’s computer or server. In this blog we are going to discuss the various techniques at your […]