One of the most daunting challenges facing any CIO today is the very real threat of a security hack that results in sensitive data getting into the wrong hands or disrupts business. All organizations – large or small, private or public – must be vigilant to protect not only the security of their data and infrastructure, but also their reputation and the bottom line.
Cybersecurity attacks are happening with increasing frequency. It seems that every few weeks a high-profile attack makes the news – Sony, Target, the Federal Office of Personnel Management (OPM), Anthem, UCLA Health, even the IRS. What’s not well known is that many cyberattacks are the result of “insider threats.”
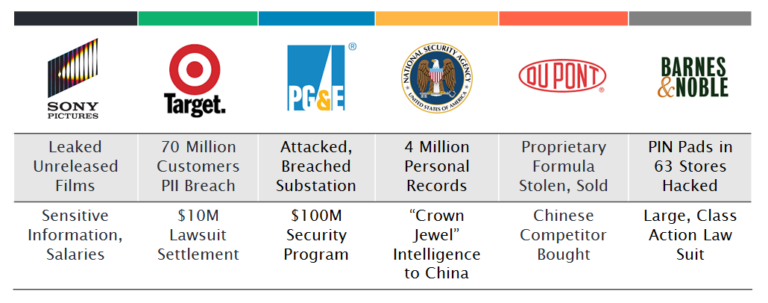
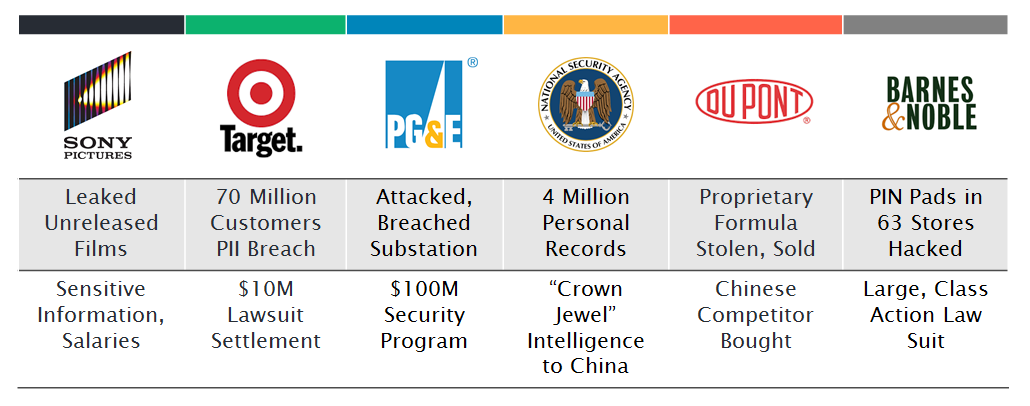
Insider threats are often underreported by organizations. However, the 2013 US State of Cybercrime Survey reported that more than 50% of respondents had experienced an insider attack, and 53% of those said that the damage from the insider attack was greater than that of an outside attack. Look at the damage these organizations incurred as a result of insider threat vulnerabilities:
When it comes to protecting against insider threats that affect data, reputation, safety and business, vigilance is key. Insider threats come in a variety of forms, but typically occur when a current or former employee or contractor exploits or exceeds his or her authorized level of network, system or data access. Not all of these threats are due to malicious intent. The majority start as simple negligence when an otherwise non-threatening individual accidentally opens the door for a malicious third party.
There are a number of areas from which insider threats can originate:
- Device Level Threats
- Network Level Threats
- User Proficiency Threats
- User Behavior Threats
- Social Media Threats
Each of these areas requires a different set of critical capabilities. I’ve seen many of GTRI’s customers grapple with the resources and knowledge to successfully defend from outside attacks. Adding a new set of capabilities and best practices to detect insider threats is asking a lot.
That’s why I am pleased to introduce GTRI’s Insider Threat Security Solution. We’ve partnered with best of breed cybersecurity companies to address threats from the device, network, user proficiency and behavior, and social media levels.
While it’s easy to rationalize that insider threats won’t happen to your organization, it has become clear that this breed of threat is pervasive and is not limited to the obvious targets of government, finance and healthcare.
Screening employees and contractors and maintaining strong perimeter security is not enough to guard against insider threats. Partnering with a trusted service provider like GTRI that can work with you to identify your needs and help you implement the best security solutions for your organization is the most effective approach to avoiding the pitfalls of this class of threat.
Greg Byles is the CEO of GTRI.