Security has always been a driving principle at Cisco Systems. From the introduction of the Pix to the ASA (Adaptive Security Appliance), Cisco has been at the forefront of the firewall market. In the intrusion prevention space, Cisco has recently acquired Sourcefire, whose Snort products are now integrated with the company’s Next Generation IPS line and whose Fire Power services are now included in the ASA Firewall.
In the Identity Management and AAA (Authentication, Authorization, and Accounting) space, Cisco has long been a player, as well, with the Secure Access Control System (ACS). The Cisco ACS has a long history of supporting both the RADIUS and TACACS+ protocols for AAA. However, this has not been true with the newer Cisco Identity Services Engine (ISE), which has only supported RADIUS for Network Access.
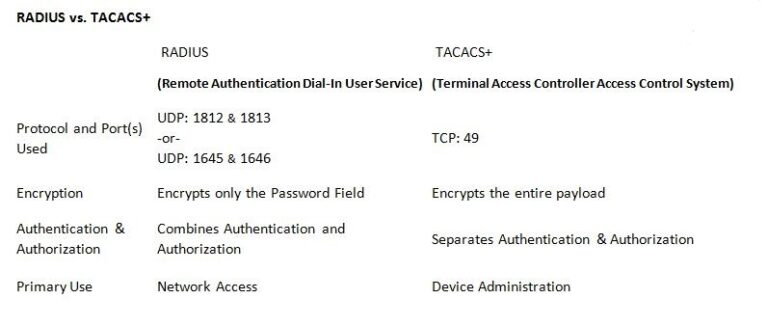
While each protocol has its own benefits, traditionally RADIUS has been used for Network Access and TACACS+ has been utilized for Device Administration. TACACS+ excels at the ability to take each AAA function (Authentication, Authorization and Accounting) and separate each one independently. This is an advantage for the transactional nature of the per command list authorization of Device Access and Administration.
The RADIUS protocol, however, is different in that aspect. RADIUS utilizes a large subset of attributes, as defined by IEEE (Institute of Electrical and Electronics Engineers), to perform functions such as applying ACLs (Access Control Lists), designating VLAN (Virtual LAN) assignment, etc. As it was designed for Network Access control, it does not separate the Authentication and Authorization AAA functions. This becomes a challenge for true 2-factor authentication, because only one request can be sent. (See RFC 3576 and how Cisco AnyConnect and Change of Authorization, or CoA, can overcome this.)
Role Based Identity Management Finally Meets Command Authorization
Now, however, with the introduction of the Identity Services Engine (ISE) 2.0, Cisco ISE now supports both RADIUS and TACACS+ protocols and design functions, and is capable of handling both Network Access and Device Administration roles.
With ISE 2.0, one of the final barriers to migration from the Cisco ACS line has been torn down. Long have Security Administrators desired to upgrade from some of the constraints of the Cisco ACS platform. Now, with the ability of ISE 2.0 to provide feature parity with the ACS line via TACACS+ support that migration ability is there (in all but a few use cases ISE is fully TACACS+ compliant).
Easier Device Administration
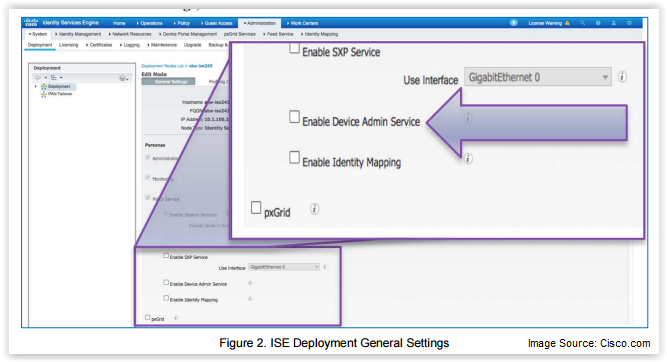
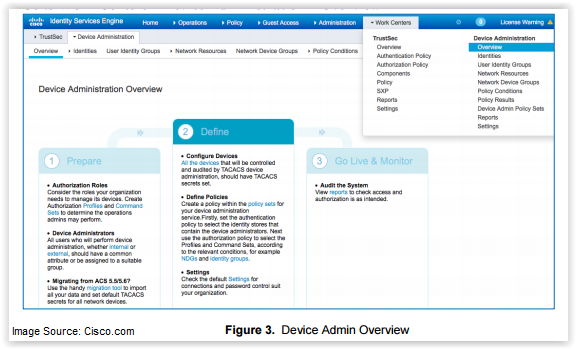
With the addition of TACACS+ support to ISE 2.0 comes the need to actually support it! Fortunately Cisco has had the foresight to create tools to better help administrate and implement a variety of Device Admin functions. One such tool is the Device Administration Work Center, which has been designed to make management as easy as possible for both new users of ISE as well as veterans. By centralizing the functions and providing easy links to important controls for customizing your system, the Device Admin Work Center makes implementing useful control policies much simpler.
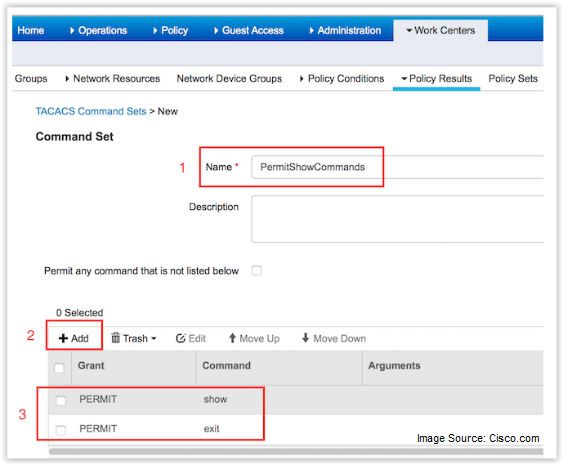
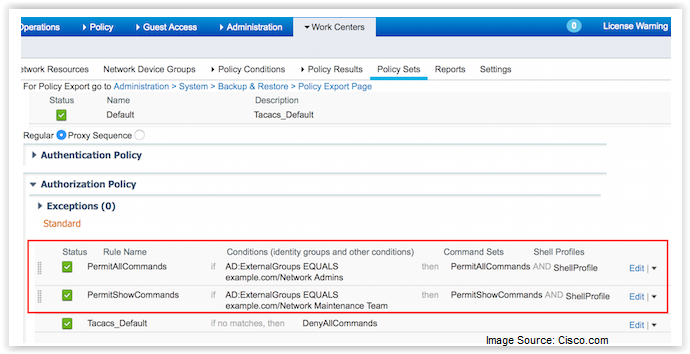
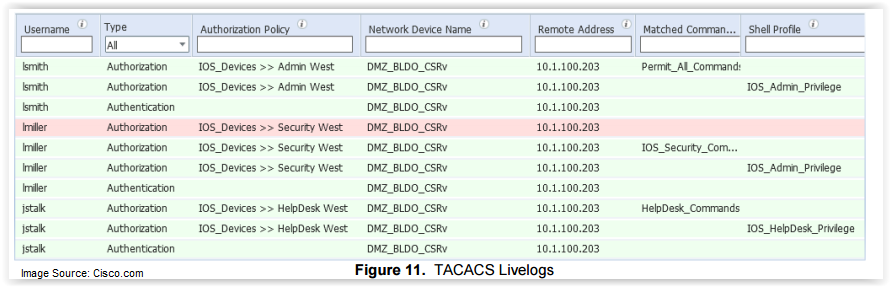
Another important feature to help implement TACACS+ in ISE 2.0 is the ability to support stackable command sets.
This function allows the administrator to independently define subsets of IOS commands, such as the variety of “show xxx” commands, into one command set. Each command set can then be chosen independently and stacked into another logical grouping, which can then be applied to a chosen user group community. By defining groups of user communities based on role and function, you can define the commands those users are allowed to perform on each device.
New Reporting Framework with Endpoint Details
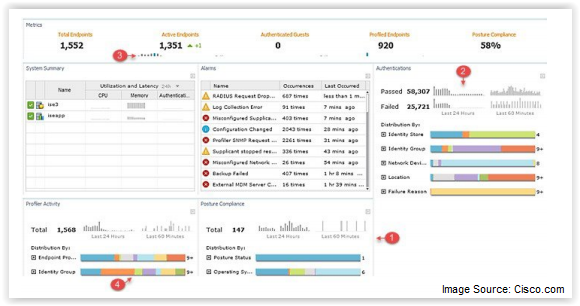
Another important development in ISE 2.0 is the reporting and monitoring tools. With the improved look and feel of the ISE Administrator Portal, several key reporting elements have been brought to the forefront for further analysis (just a link click away!). ISE node monitoring, event alarm notification, authentication, and posture compliance reporting all display current information in 60 minute/24 hour snapshots right from login to the administrative graphical user interface (GUI).
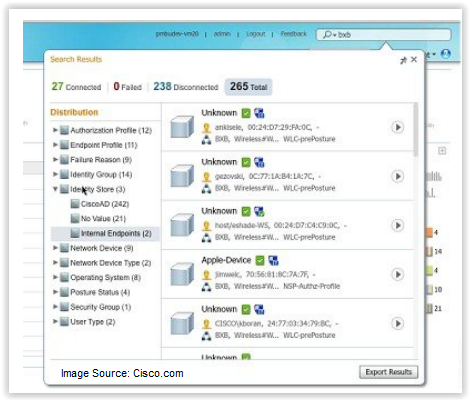
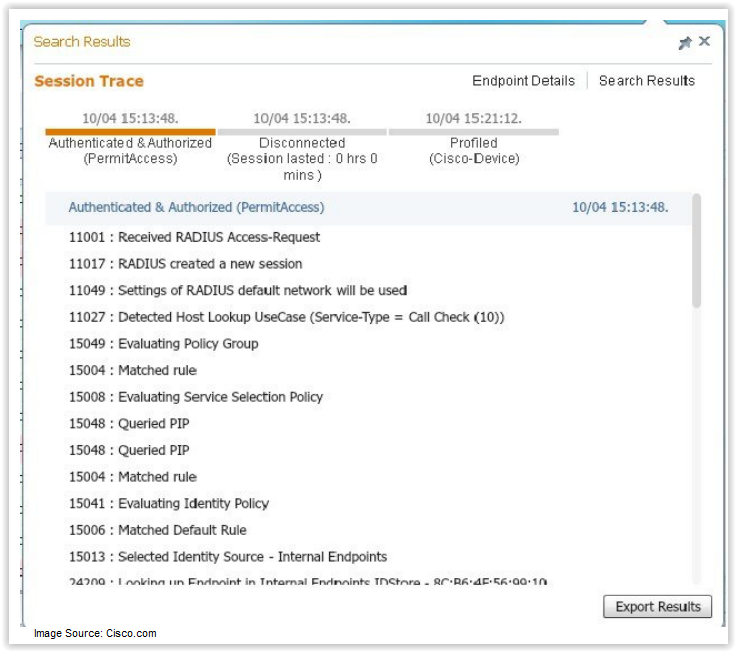
Adding to the monitoring functionality, ISE 2.0 now includes endpoint drill-down ability with detailed information on the session. By inputting user identity information in the search toolbar, you can now correlate events from the Live Logs and gather data about the endpoint in question. This level of detail and ease of traceability make ISE 2.0 an ideal reporting and troubleshooting tool.
Conclusion
Cisco has come a long way with the Identity Services Engine (ISE) platform. Role-based access control principles were applied quite well to perform Network Access with the RADIUS protocol. However, backward compatibility with the Cisco ACS platform — primarily the inclusion of the TACACS+ protocol and the ability to perform command level authorization and Device Administration — has long been a cry from security engineers in the field.
That cry has now been heard by Cisco. ISE 2.0 is here and available. Take some time to look at the new Portal Management for BYOD and MDM implementations. When you’re ready to look at Cisco’s ACS migration plans, give us a call and we’ll help you determine if it makes sense for your organization.