In the previous blog post on DNS traffic inspection we covered how attackers target DNS systems. Attackers use Fast-Flux DNS techniques to rapidly change the server’s hosting malware. Attackers control malware to change the DNS behavior on the end-user’s computer or server. In this blog we are going to discuss the various techniques at your disposal to help gain visibility to these types of attacks. We also cover techniques for stopping these network security incidents right from the start of infection.
Response Policy Zones (RPZ)
One method to increase the security of an enterprise via DNS is to use Response Policy Zone (RPZ) mechanisms. RPZ is a method of sharing DNS firewall information with DNS software like BIND. Based on the validity of the queried domain, the recursive DNS resolver can chose to allow or block the query, thus blocking the connection from taking place. Organizations can pre-populate the policy with malicious domains or addresses or could obtain a “feed” of malicious Internet sites from another source. This is a type of reputation filtering but it is DNS-based rather than implemented in the firewall or IPS. This type of a solution can help prevent inbound unsolicited spam e-mail and help prevent end-users from connecting to sites hosting malware or botnet command and control networks.
Infoblox DNS Security Solution
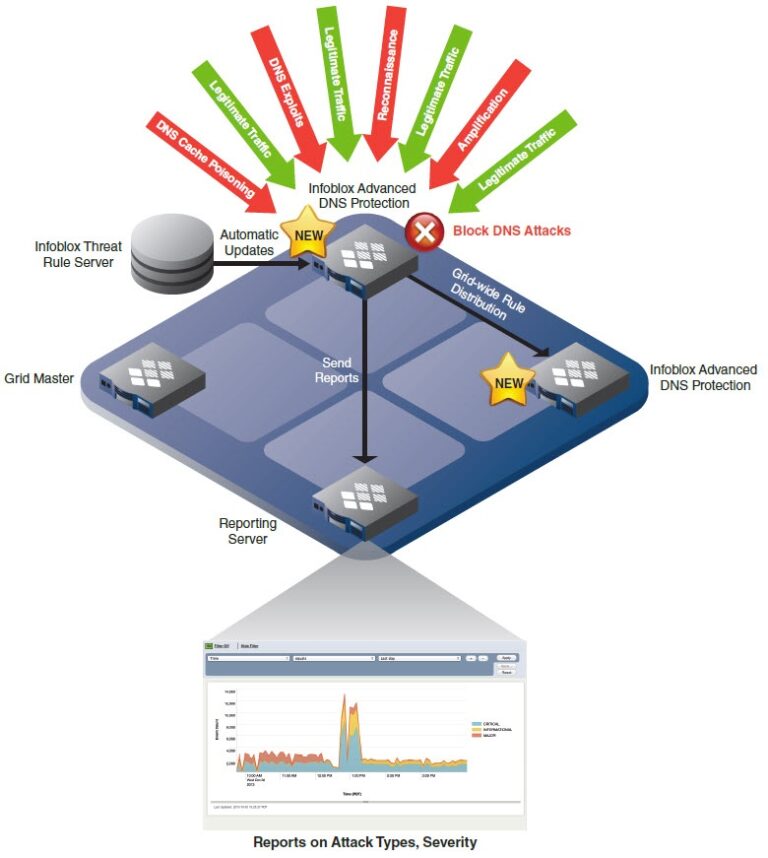
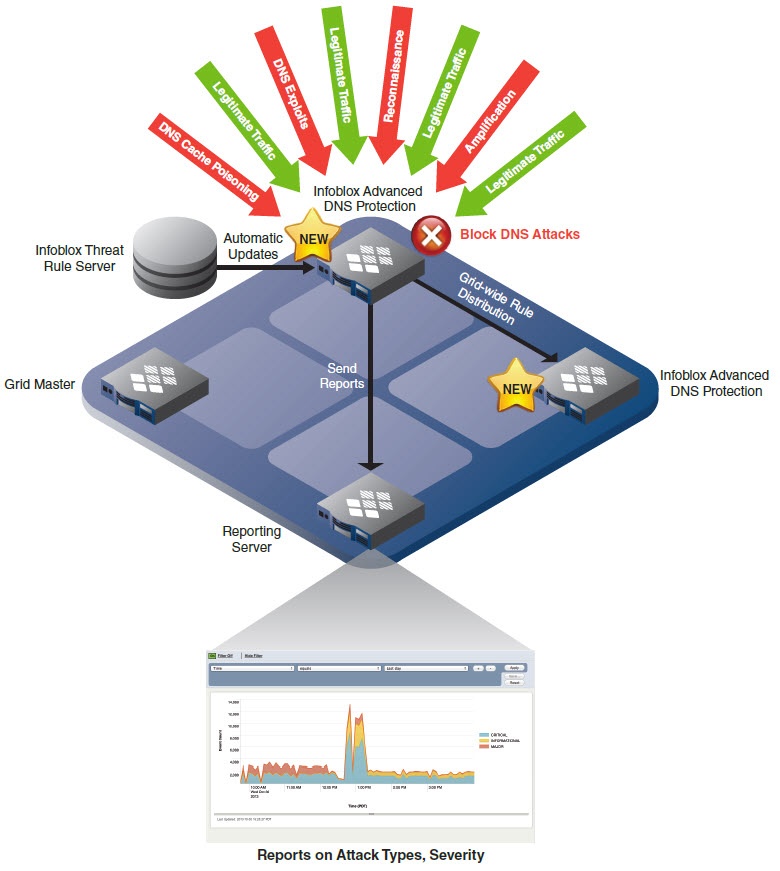
The first component of Infoblox’s secure DNS infrastructure is the Infoblox Advanced DNS Protection. This is a set of techniques that help thwart the most common attacks against the DNS infrastructure itself. The Infoblox DNS servers can detect, mitigate and alert if they are being attacked. The DNS security settings are configurable and tunable to suit the organization. Infoblox DNS systems are security hardened and even meet the government’s EAL-2 certification. The Infoblox fortified appliances provide high availability and clustered resiliency through the Infoblox Grid system.
Following is a diagram of the Infoblox Advanced DNS Protection system.
Source: http://www.infoblox.com/products/dns-dhcp-services/grid
The Infoblox DNS servers block the attacks while maintaining proper operation for the legitimate queries. The reporting server gives the DNS administrator up-to-the-minute reports on the security status and performance.
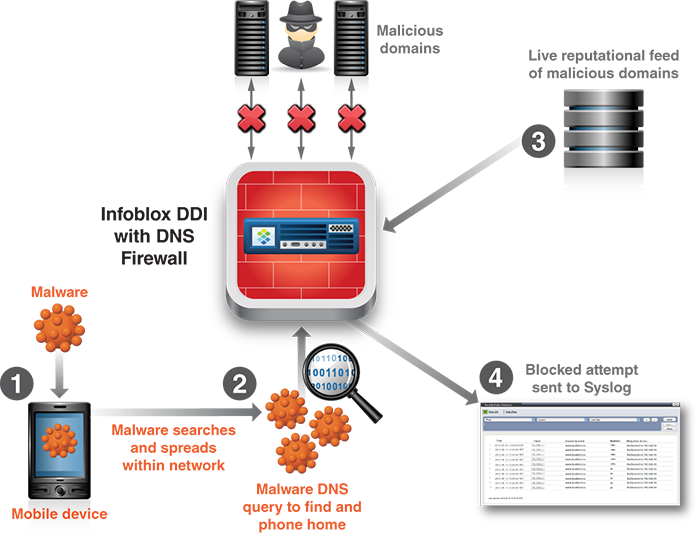
The second component of Infoblox’s secure DNS infrastructure is the Infoblox DNS Firewall. The Infoblox DNS security firewall component performs DNS forensics and prevents systems from communicating with malicious Internet sites. It does this by integrating with your security perimeter system and by using RPZ technology to stop the DNS request from allowing the attack connectivity to take place. The Infoblox DNS Firewall can easily integrate with the FireEye’s malware protection system.
Following is a picture of how this DNS firewall operates.
 Source: http://www.infoblox.com/products/infrastructure-security/dns-firewall
Source: http://www.infoblox.com/products/infrastructure-security/dns-firewall
The DNS firewall inspects all DNS traffic that is passing in and out of an organization. It is able to find the “needle in a haystack” and disarm malware before it starts to operate. The DNS firewall then provides reports and data extracts to other Security Information Event Management Systems (SIEMS) for security practitioners to take action to remediate the infections.
Operationalizing DNS Inspection and Firewalling
Organizations need to start to realize that they may not be able to stop the malware from entering the organization using traditional firewalls and IPS systems. Firewalls typically allow TCP port 80 and 443 (Web browsing), and TCP and UDP port 53 (DNS traffic) to pass through unobstructed. Most malware leverages these weak outbound security policies to infect an enterprise’s internal computers. If the assumption is made that the malware is already on the internal systems, then the focus should be on rapid early detection and remediation. The first activity that a piece of malware will perform is to make a DNS query for an Internet-based system. This could either be to “phone home” and connect to a command and control system or make a connection to download additional malware. It may not be possible to prevent against the initial infection, but DNS provides that first evidence of an attack.
Most organizations seem to think that the job is done once the security system is procured. However, we know that incorporating people and processes with the technology yield the best results. Organizations need to consider the operational aspects, reports, and process for remediation (workflow) when these types of DNS attacks occur.
The good news is that with these Infoblox DNS security features, it is easy to tie this into a process of continuous security monitoring. In fact, U.S. government organizations have a goal to implement Continuous Monitoring of security threats. To this end, NIST has drafted a document describing this approach. The Infoblox DNS Firewall and the Trinzic Reporting utility for Splunk could give added situational awareness to any IT department.
Summary
Inspecting DNS packets on your network is a valuable forensic capability that you should obtain. DNS firewalling gives organizations the ability to quickly detect malicious incidents occurring in their environments and arm them with the ability to prevent these attacks right from the start. Even if you acquire this DNS firewalling and forensic capability, your organization will still need to work through the operational aspects of owning such a system. Acquiring the technology is just one parameter of the equation. Having well-trained people who know how to use a well-documented and disciplined process will maximize the investment and produce the best results.
This post originally appeared on the Infoblox blog at https://community.infoblox.com/blogs/2014/02/18/improved-security-through-dns-inspection-part-2