Getting on Top of Information Security at Cisco Live 2015

It’s that time of year again. Project and implementation rollouts across the country are placed on a temporary pause and the masses of Cisco technology wizards descend upon Cisco Live US (#CLUS), this year held again in San Diego, CA. Every year Cisco brings a new set of products, services and platform improvements to discuss […]
Using Domain Keys Identified Mail (DKIM) to Improve Email Security
Today, enterprises have a heightened awareness of their network security measures and are concerned about the cyber threats to their organization. With the emphasis on Internet security due to recent highly publicized corporate security breaches, enterprises are re-evaluating their security measures and increasing their funding of IT security initiatives. Security practitioners applaud organizations that are […]
Can SDN Switches Replace the Firewall?

One of my 2015 technology predictions was that more companies would start to deploy Software Defined Networking (SDN). Although the concept originated in the mid-1990s, SDN is finding an eager audience today as organizations seek a more dynamic, adaptable and cost-effective solution for their intensive data transfer requirements.
Security in the Data Center with Cisco ACI
I was recently selected to be a member of the Cisco Champions team in 2015. This is truly an honor and gives me the opportunity to share my thoughts on IPv6, data center security and networking on the Cisco Communities blog site.
Using Security Reports to Improve Your Information Security Practices

Security was a big buzzword in 2014 thanks to a number of well-publicized and, in some cases, very damaging breaches. Hackers are getting smarter and more resourceful, and many IT departments are being overloaded with their attention divided in a million different ways. Yet, we have to be careful not to “throw the baby out […]
Identifying Vulnerabilities in Software Defined Networking (SDN) Layers
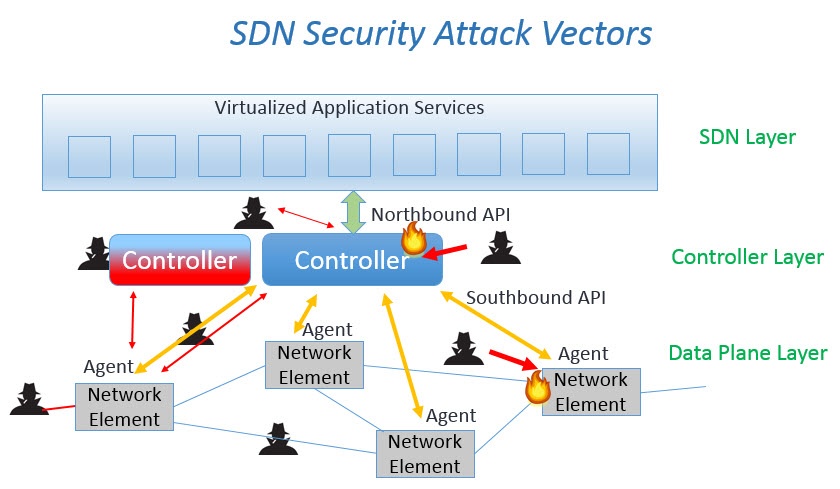
Software Defined Networking (SDN) is a new way of providing virtualized networking. As with any new technology, potential security vulnerabilities need to be anticipated and addressed as much as possible. Of course, we can only try to anticipate what aspects of SDN hackers may target. The protocols are new, the controller software is new, and […]
Splunk Partners and Practitioners Unite at .conf2014

Securely Enabling ICMPv6 Router Advertisements on Your IPv6 Network
When a dual-protocol host joins a network, it sends an ICMPv6 (type 133) Router Solicitation (RS) message to inquire about the local IPv6-capable router on the network. The local router is tuned into the ff02::2 (all-router’s multicast group address) and will receive the RS message. In response to the RS, the router immediately sends an […]
Securing Open DNS Resolvers Against Denial of Service Attacks
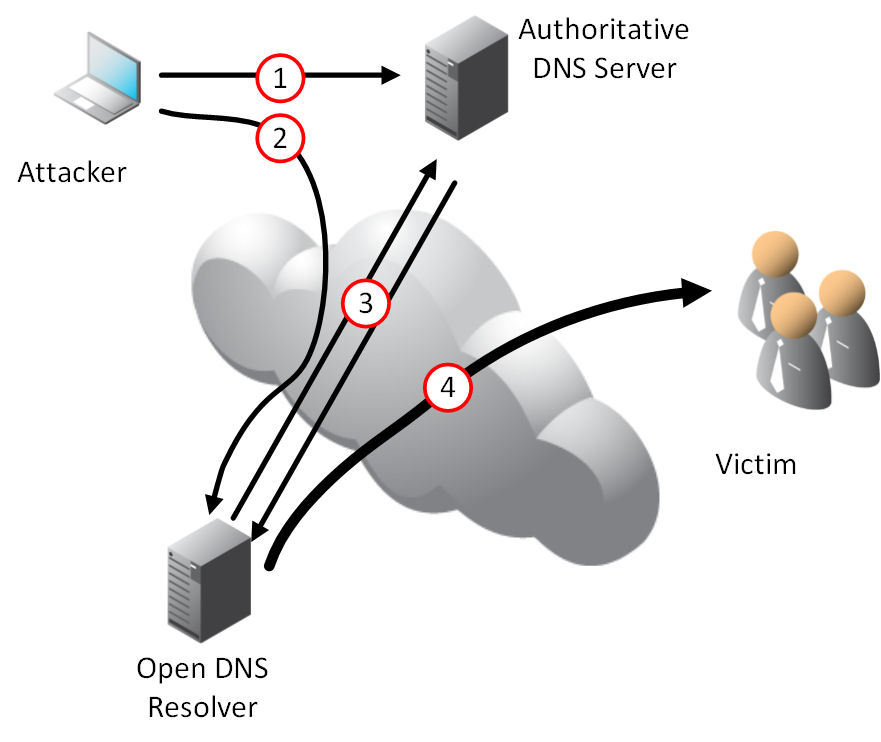
The Domain Name System (DNS) has been the target of many types of attacks in recent years. Authoritative DNS servers are exposed to the Internet and generally allow queries from all IP addresses. However, DNS resolvers are typically internal to an organization and allow queries only from the internal clients they serve. DNS resolvers that […]
Improved TLS / SSL Security with DANE
You may be familiar with the benefits of using DNSSEC to provide authentication and integrity for your DNS information. DNSSEC is a lot like dental floss: we all know that it is good for our health, but few enterprise organizations actually put forth the effort to implement the best practice. If organizations do not use […]