Expanding Insider Threat Security with Employee Training and Awareness
When you think of “insider threats,” what comes to mind? Perhaps a disgruntled employee looking to hurt the organization or someone selling company secrets. But not all insider threats have malicious intent. Human error is certainly a leading cause of data breaches. Many incidents occur as a result of a mistake on the part of […]
Addressing the Cisco ASA SNMP Remote Code Execution Vulnerability
As you have probably seen, there has been much in the news lately about the EXTRABACON exploit released by a group of hackers called the Shadow Brokers, who supposedly acquired the exploit (and other cyber weapons) from a different group of hackers, the Equation Group, which is rumored to be affiliated with the National Security […]
What’s in Your Email?
Most of us wouldn’t want anyone snooping around our personal or company emails. Yet email security breaches are becoming more common. Consider these recent situations:
How not to Fall Victim to an Insider Threat
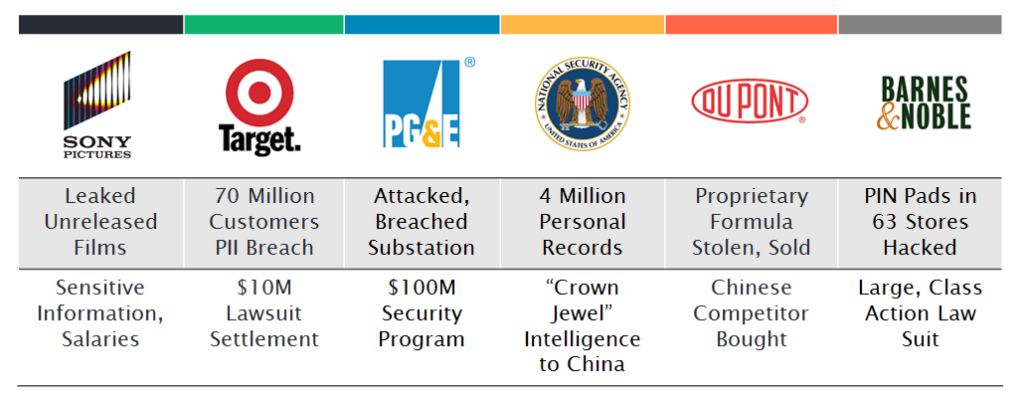
One of the most daunting challenges facing any CIO today is the very real threat of a security hack that results in sensitive data getting into the wrong hands or disrupts business. All organizations – large or small, private or public – must be vigilant to protect not only the security of their data and […]
Insight Out: The Fundamentals of Using Data in Splunk
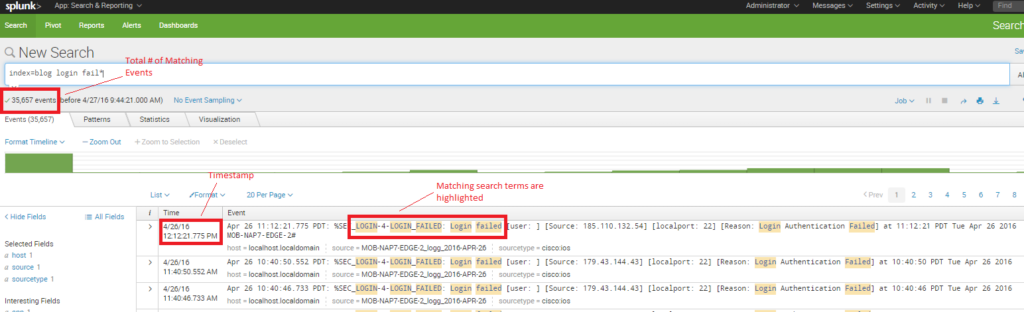
In the last post on this topic, my fellow Splunk architect, Micah Montgomery, gave an overview of one of the most important parts of getting going with Splunk: Getting Data In. He outlined a basic process and framework to follow when you need to successfully get data into Splunk so that you can make that […]
Hardening Splunk Against SSLv3 POODLE Vulnerability Scans

As a system administrator, it is part of the job to address the vulnerabilities that leave a network open to security incursions. When looking for these vulnerabilities, it’s not uncommon to find “false positives.” Vulnerability scanners are notorious for not considering the entire system architecture, reading solo system configurations and reporting vulnerabilities that don’t actually […]
Understanding Your Organization’s Role in Cloud Security
Whenever you stay in a hotel, you likely take certain things for granted, one of which is security. You expect that the management will have taken reasonable steps to keep guests and their valuables safe during their stay. You expect that no one else will be given a key to your room, and that you […]
GTRI, root9B and Ziften Announce Cyber Alliance to Provide Next-Gen Security Solutions and Services
Businesses and governments face challenges in the development of an integrated strategy to protect their environments in today’s increasingly complex threat environment. We at GTRI, with our partners root9B and Ziften, are announcing a strategic cyber alliance to help customers respond to these increasingly complex challenges.
Impressions from Cisco Live! Europe 2016 in Berlin

I had the opportunity to attend Cisco Live! Europe 2016 (CLEUR!), held February 15-19 in Berlin. A combination of meetings with customers and partners provided for some fortuitous Europe-bound timing. This wasn’t my first time to Live! but it was my first time to Live! in Europe. I’ve always liked Live! as an opportunity to […]
Next Generation Identity Management Using Cisco Identity Services Engine (ISE) 2.0
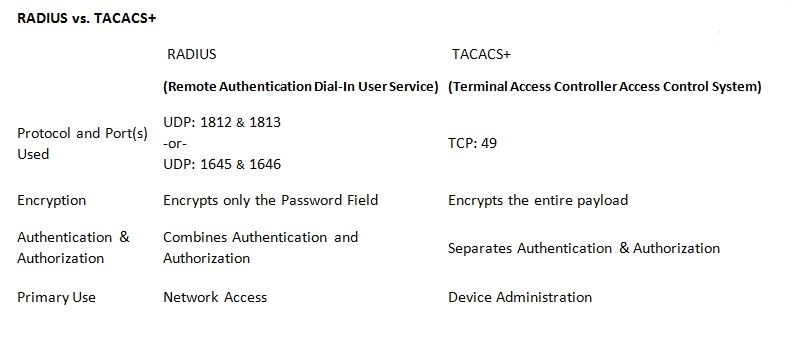
Security has always been a driving principle at Cisco Systems. From the introduction of the Pix to the ASA (Adaptive Security Appliance), Cisco has been at the forefront of the firewall market. In the intrusion prevention space, Cisco has recently acquired Sourcefire, whose Snort products are now integrated with the company’s Next Generation IPS line […]