Splunk Product Timestamp Issue Solution

What is the issue?
Splunk .conf2016: Learn how to Leverage Splunk’s Ecosystem for Your Own Products
I am excited to be a speaker at Splunk .conf2016 (#splunkconf16), which will be September 26-29 in Orlando, FL. I’ll be joining Michael Franke, Senior Director Product Management for SecureAuth Corporation, to discuss how their custom Splunkbase app improved their customers’ visibility into security data and response times to security incidents.
Fake It to Make It: Tips and Tricks for Generating Sample Splunk Data Sets
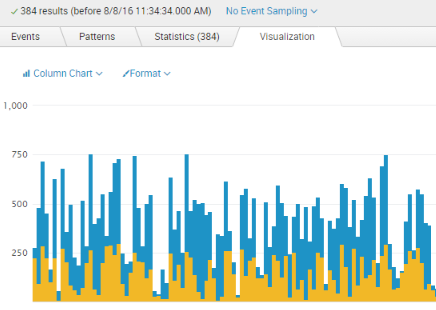
As you continue to work with Splunk and the number of underlying use cases within your organization grows, you will ultimately encounter a situation where you need to generate some “fake” data. Perhaps you need to create a visualization to use for a proof of concept; perhaps you are trying to master a specific search […]
Avoiding a “Train” Wreck: Getting the Most Out of Splunk
In a bit of a departure from our recent technical blog posts, I’d like to focus instead on getting the best value out of your Splunk investment. Many times, most of the effort is concentrated on getting data into Splunk with little regard to what end users need to know in order to use it […]
Getting Even More Data In: Splunking Outside the Box
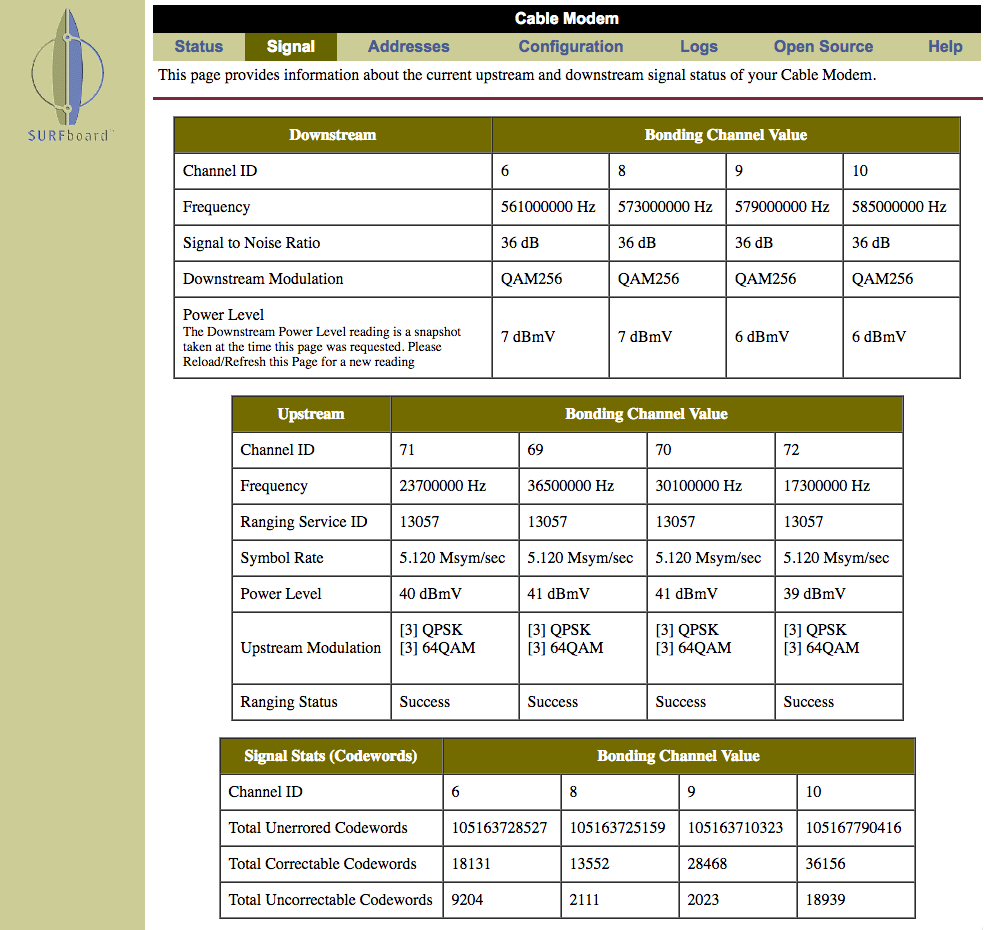
In the last couple posts on this topic, Micah Montgomery gave an overview of getting data into Splunk, and Scott DeMoss gave an overview of getting data out of Splunk. In this post, I am going to go “outside the box” and cover how to use Splunk scripted inputs to get data from atypical sources […]
Using Splunk Scripted Inputs beyond Data Collection
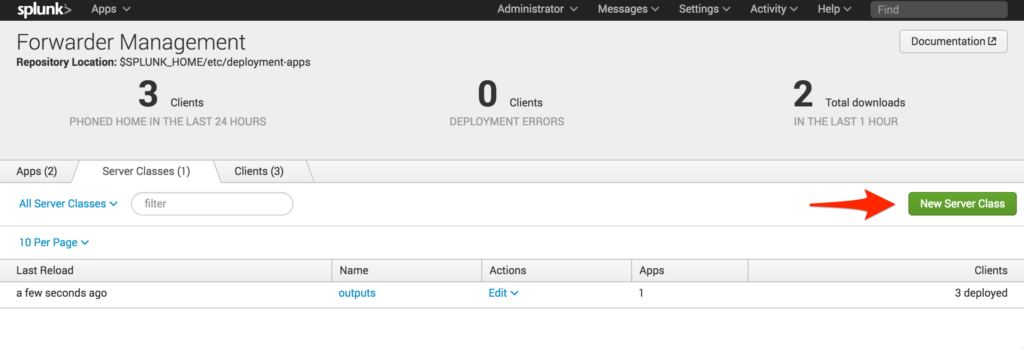
On April 18, 2016 Splunk announced that the default root certificate used in pre-6.3 Splunk Enterprise, Splunk Light and Hunk will expire on July 21, 2016. As a result, these instances will no longer be able to communicate with each other after July 21. This Product Advisory only applies to pre-6.3 versions of Splunk. The […]
Insight Out: The Fundamentals of Using Data in Splunk
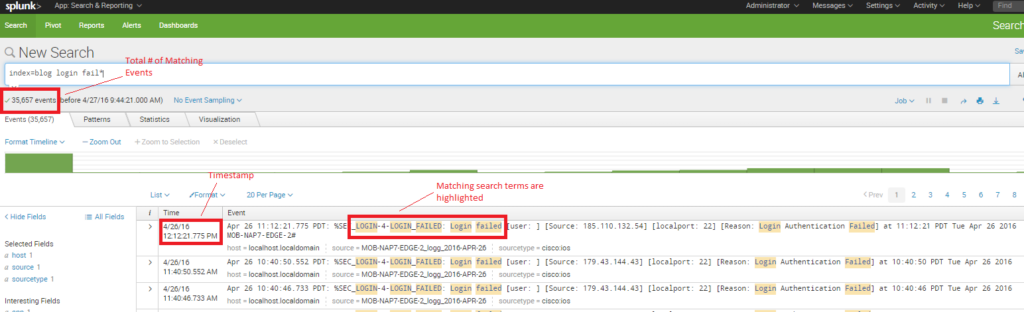
In the last post on this topic, my fellow Splunk architect, Micah Montgomery, gave an overview of one of the most important parts of getting going with Splunk: Getting Data In. He outlined a basic process and framework to follow when you need to successfully get data into Splunk so that you can make that […]
Hardening Splunk Against SSLv3 POODLE Vulnerability Scans

As a system administrator, it is part of the job to address the vulnerabilities that leave a network open to security incursions. When looking for these vulnerabilities, it’s not uncommon to find “false positives.” Vulnerability scanners are notorious for not considering the entire system architecture, reading solo system configurations and reporting vulnerabilities that don’t actually […]
Getting Data In: The Overlooked Art of Cooking Up Splunk
Here at GTRI, when we talk about Splunk we divide it up into two major tasks – getting data into Splunk (i.e., data ingest) and getting information out of Splunk (i.e., search, alerts, dashboards). These tasks are equally important to getting value from Splunk, and, after all, that’s the whole point of the exercise in […]